Have you ever noticed any of the following on your PC?
- Processes running abnormally slow
- Random ads popping up in the background
- Your homepage suddenly changed but you didn’t change your homepage settings
- Your firewall and antivirus are suddenly disabled
- Suspiciously high increase in internet traffic
It is possible that your PC has been infected by malicious software, or malware.
How can this happen?
Attackers will try to hide malicious code and get your computer to execute it. Malware is commonly delivered through the following channels:
Websites
Some websites may host malware; when you visit such a site, it will force a download in the background.
- They may have pop-up boxes that say something is wrong with your PC – DO NOT click anywhere on these. Just clicking anywhere on them (even cancel, close or X) may install malware or spyware in the background! Try closing your browser tab instead.
If you cannot close your browser tab, safely close your browser window by:
On Mac
- Simultaneously press option, command, W buttons on your keyboard
On Windows
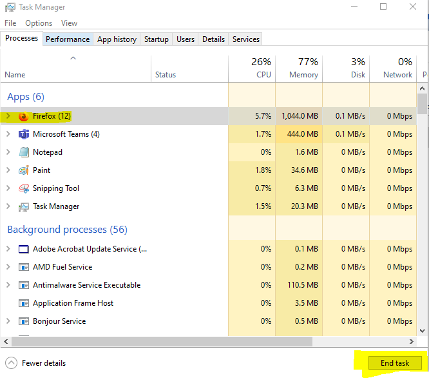
- Simultaneously pressing CTRL ALT Delete buttons on your keyboard
- In the menu that is brought up, click on “Task Manager”
- In the Processes tab, select your browser and click “End Task” on the bottom of the window.
Infected USB drives
When plugged in, the malicious code will run and infect the PC.
Downloads
Always download software from official sites. Third party websites can host infected versions of software, which may seem like they run just fine but have installed additional unwanted code on your PC without your knowledge.
Some examples of downloads to avoid are:
- Torrent/pirated copies of software, music, or videos
- DLL download websites
Email attachments
It may look like a PDF, Word, or Excel file is attached to an email, but any file could contain malicious code. It is best not to download or open attachments from suspicious emails.
- If you do open a malicious Word or Excel document, be wary if there is a message that asks you to “enable editing” – this will give permission for ANY code hidden into the document to run!
What you can do to protect yourself
- Keep your browser up to date. Some browsers will try to warn you of malicious websites and block some exploits. While they will not catch everything, keeping them up to date helps improve what they can detect.
- Minimize the user of browser plugins – while these may be convenient, they may have out of date or vulnerable code that can be exploited.
- Never plug in untrusted USBs
- Always log out of your accounts when you are done using them. Lock your PC if you have to step away from it for a bit. Do not leave your account open and unattended.


